10 steps for everyone to secure your email and online accounts
How much of your own life is now online?
For most people it’s a high proportion: your banking details, access to your pension and online share trading account, your social life via Facebook and other social media, your subscriptions to paid and unpaid news sites, loyalty schemes about your buying and flying habits, your online shopping via Ebay and other online retailers and payment systems like Paypal, your business and personal communications via your email account, your company’s digital assets via your work login, your social security details and other government revenue collection and licensing systems – even that blog that nobody knows about.
And just like someone walking into your house and walking out with all your valuables, the ability for someone to walk in and take over your life primarily rests on a single key, your password (but with way more value stored online than in your house).
Many security people reading this would claim this is an over-simplification (even though this article is not written for security experts).
Surely, they’d say there’s two keys the thieves/casual hackers/spooks need: your username and your password. And your password may be different on different sites.
But security experts are not most people. For most people their username is often their email address, and their password is often the same across different sites, or the same with small variations, for instance rotation patterns on keyboards or a common password with date-related variations.
More often than not people use the same passwords across different elements of their life (i.e. once you walk in the door you have access to every room in the house) and there are even easily available lists of common passwords that the population at large uses. And your email account is posted online somewhere (your corporate email address is usually guessable just by looking at the convention your company uses for other email addresses posted on your firm’s website), and from one email account you can often get to others. And even where your passwords are different, with access to just your email account your passwords can be reset on other sites at will by a hacker.
If you place value on access to all these different components of your life and you wouldn’t hand your house keys and address to a stranger in the street then you need to take responsibility for your passwords being safe – it’s not that you need to be paranoid, it’s just that you need to not be stupid.
Here’s some must-dos in descending order of importance.
1. Use a password management application
On both your smartphone and computer with a strong password. Why? If you don’t do this you are going to end up re-using passwords and even where you don’t share, wasting time retrying and resetting passwords. I have over 240 passwords stored in my password management app – there’s just no other way to handle it unless you have a photographic memory. If you don’t have a password management app you are re-using passwords (see below). The password management app will encrypt all the passwords so if your device is stolen they are all unreadable – do not use an Excel spreadsheet or the like.
2. Do not reuse passwords
The alphabetical list of major websites hacked is long and getting longer every day from Last.FM to LinkedIn just to mention a couple in the ‘L’s. And these are major players who are able to afford good security people and who maybe even adopt good password management strategies like not storing passwords in plain text. However many of the sites you regularly access can’t afford good security and do not adopt good practices. If you re-use passwords people who’ve hacked those sites (and other hackers who access the online databases of hacked passwords from sites) have both your email address and your password and then can use that information to reset passwords on other sites you use.
3. Change your passwords for services that you use regularly (at least once a year)
Even with the best will in the world you may reveal key passwords (for example by using a friend’s computer that is infected with a keylogger virus). If you are lucky however, by the time the information gets around to being used you may have changed your password.
4. Do not pick up your email insecurely
Huh? Given that access to your email account is often the key to resetting your passwords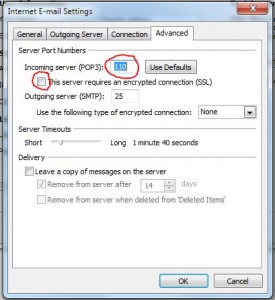 (the hacker can reset the password have the reset link sent back to your email account that he/she has hacked) it is important that you do not allow other people into it.
(the hacker can reset the password have the reset link sent back to your email account that he/she has hacked) it is important that you do not allow other people into it.
The problem here is that as life gets more mobile it is easier and easier to hack into people’s email accounts. Why? Because when you pick up email over the airwaves, for example via your smartphone or via your laptop over a WiFi computer in an airport or coffee shop, you might be using an insecure protocol to do it like POP3 (I know this is jargon but bear with me) and not an encrypted connnection.
On WiFi networks it’s possible to monitor all traffic going over the network whether or not it is intended for your computer and it is really simple to see what your email address is and what your password is, you just need to download a simple traffic snooping package and then look for the password which is helpfully labelled as such.
I’m not giving away anything here – the bad guys already know this stuff and an infinitely patient computer is probably snooping 24×7 at your local airport as we speak – and in certain countries is probably installed by the government as part of the airport infrastructure.
If your computer never goes anywhere but is wired into a router at home do you have WiFi at home as well? Better make sure your home WiFi is secure or you could be vulnerable to the same problem there – although it is less likely unless you live in high density housing. Even though your computer may be directly connected to the router the traffic will still be broadcast over your home WiFi network.
Take a look at the mail settings on your smartphone and laptop and see whether the SSL setting is checked (or have a friend do it who knows something about email). SSL encrypts the connection end-to-end so the snooper cannot see your password.
If your ISP or corporate network doesn’t support secure mail you have a big problem – you literally should be with another ISP and/or your corporate IT department is clueless.
Note that access to your email can just be physical access to your device. If your smartphone/tablet is stolen or lost and you think it might be easily unlockable then someone can both access your email and even reset your passwords where or confirm banking transactions where a confirmation SMS code is required. In such circumstances you should change your email password as fast as possible or have your network admin temporarily disable the email account ASAP.
5. Install a good antivirus product
You can have the best passwords in the world and a good password management application, but if the bad guys are looking over your shoulder as you enter credentials into your online banking website this is all for nothing. Software exists (and is readily available) to do just this: to record both your screen and your keystrokes. And many of the emails you receive on a daily basis either with attachments (many of which you will never see because they are filtered out by your corporate network or ISP) will be designed to fool you into installing this software or send you to a web address where there is malware planted to download and install automatically on your machine if it is not patched.
6. Make sure you are up to date with patches
If you’ve just turned on a computer or a smartphone that’s been sitting in a shop or your cupboard for 6 months make sure it’s updated before you start using it.
And it’s not just the operating system, commonly used applications like Flash or Acrobat should all be updated. One of the most common routes to get malware onto a machine is old Java installations – make sure the newest version is installed or remove it.
7. If your computer has been infected with a virus you really should have it reinstalled from scratch
Once your machine is infected with a virus many security experts would say it is insecure even when it has been supposedly ‘cleaned’ with antivirus software.
They’ve got a point. You should have real reservations about the security of machines that have been infected even though like everyone I’ve ‘cleaned’ a machine and continued using it because of lack of time or lack of suitable backups to restore from (some of which could reinstall the virus with the backup). A lot of the time malware will have multiple payloads. Just because some of them have been found that doesn’t mean all of them have. A smart virus writer might even play to this tendency by putting some straw man malware on your computer that can be cleaned so you think you’ve cleaned it all.
Some of the viruses out there have been become extremely sophisticated, encrypting themselves in memory, creating randomly sized files, loading before the operating system (rootkit viruses) and even storing themselves at the end of your hard disk in empty space but without creating an entry in the file system so that the virus scanners do not even have a file to scan.
You’ve got to assume too that expert virus writers will probably test their viruses against the major security vendor’s software.
8. Be suspicious
If you get an email saying your Paypal account has been suspended (“click this link”) or you get an email from one of your friends promising hitherto unknown clips from the Boston bombing (and your friend aint the type to wallow in that sort of stuff) don’t fall for it. Studies of antivirus software suggest that detection rates might be as low as 25% of viruses (we just have to hope the most common 25%) so they are definitely not infallible. Exercise common sense when opening mail or going to links sent to you, or installing downloadable free/cracked versions of Call of Duty Modern Warfare 2 (the war might well start before the game does). High demand items are all excellent ways to get your malware onto lots of machines.
9. Do backups
As the saying goes you don’t need to do them if you don’t mind losing your data.
10. I’ve got a Mac / sick dog do I really have to take steps 1 through 9?
No, the tips above may not be appropriate to you. If you’re the sort of person who leaves your front door unlocked when you go out of the house and a sign on it saying ‘help yourself’ the steps above are definitely overkill. However if you wouldn’t be comfortable leaving your house like that then don’t leave yourself open to online theft either.
There is some protection in running an obscure operating system but Apple doesn’t fit that criteria – you need to move to something way more obscure.
This article filed under the following 'Interest' categories (click category for more) Hate pets


